What is Azure Firewall?
Azure Firewall is a managed, cloud-based network security service that protects your Azure Virtual Network resources. It's a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability.
You can centrally create, enforce, and log application and network connectivity policies across subscriptions and virtual networks. Azure Firewall uses a static public IP address for your virtual network resources allowing outside firewalls to identify traffic originating from your virtual network. The service is fully integrated with Azure Monitor for logging and analytics.
To learn about Azure Firewall features, see Azure Firewall features.
With NSG's or ASG we cannot write policies based on Domain names, but azure firewall supports restricting traffic based on domain names. This can be useful when we want to restrict users from accessing a particular website. If that particular website doesnt have a static IP address or an address that doesnt change everytime then restricting traffic can be a problem. So we can block access based on the domain name.
We can filter traffic that flows into or outside the Vnet using an azure firewall. It also has features like Automatic threat intelligence that sense any threats to the VNET. Azure Firewall needs to have a dedicated subnet called the AzureFirewallSubnet. We can use azure firewall to RDP into a VM also.
Controlling outbound network access is an important part of an overall network security plan. For example, you may want to limit access to web sites. Or, you may want to limit the outbound IP addresses and ports that can be accessed.
One way you can control outbound network access from an Azure subnet is with Azure Firewall and Firewall Policy. With Azure Firewall and Firewall Policy, you can configure:
- Application rules that define fully qualified domain names (FQDNs) that can be accessed from a subnet.
- Network rules that define source address, protocol, destination port, and destination address.
Network traffic is subjected to the configured firewall rules when you route your network traffic to the firewall as the subnet default gateway.
Create a VM
In this demo we will create a VM without a public IP address and will RDP into it using an azure firewall. We will create a VNET with 2 subnets. One of them will have the VM and the other one is allocated for the azure firewall.
We will have a route table that has a rule that allows traffic from the internet into the firewall. Next we will associate the firewall with the subnet that contains the VM. Then we create a NAT policy such that any request from the internet is then routed to the firewall. The rule creates a translation such that any request to the firewall from the internet to a port that is exposed on the firewall is translated to the private IP of the VM and the port that we want to access on it (3389 in our case).
Step 1
This VM should not have any inbound ports (3389) and any public IP address. Subnet1 will have the VM and AzureFirewall will contain the azure firewall.
Step 2
Step 3
Next we would need to create a route table and associate the subnet that has the VM in it. This enables all the traffic to/from subnet1 to go through the firewall.
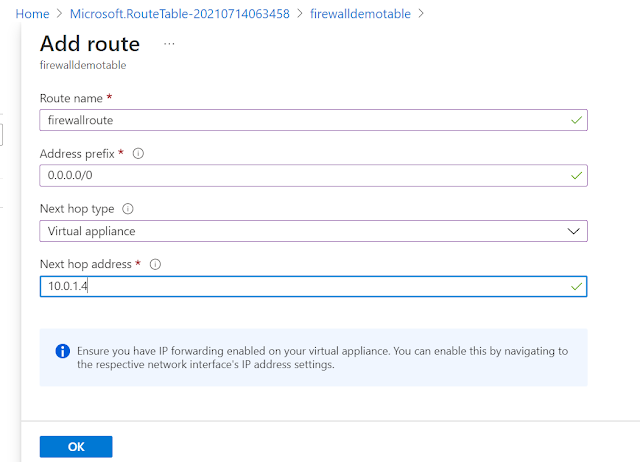
Step 4:
Here we are create a route such that any request from the internet (0.0.0.0/0) must go through the firewall which acts as a virtual appliance. Next hop address is the private IP of the firewall.
The route states that any traffic from the internet should go to the firewall. Next we will associate this route table with the subnet that has the VM. So any traffic from the internet to any resource in subnet1 should be routed through the firewall.
We then associate the route table with the subnet that contains the VM.
Step 5:Add A NAT(Network Address Translation) Rule.
NAT allows a single device, such as a router, to act as an agent between the Internet (or public network) and a local network (or private network), which means that only a single unique IP address is required to represent an entire group of computers to anything outside their network. NAT replaces the source or destination IP addresses in packets with other IP addresses. NAT rules are matched to allowed connections after Access rule matching.
This rules routes any request from my IP to the VM through the Firewall.
SourceAddress: Ur public IP
Destination Type: IP Address
Destination: Firewall IP Address (public IP)
Translated Address: VM Private IP
Translated Port: 3389 (RDP)
Destination Port: 4000 (port we want to map with 3389)
This rule will enable my IP address to RDP into a VM that has no public Ip but has the RDP port exposed through an azure firewall. We create a NAT rule such that the actual address and port of the service that has to be exposed can be masked with the destination port and the IP address of the firewall. We can similarly create another rule and expose port 4002 for RDP as well.
This is the application rule that allows outbound access to www.google.com.
- Open the Test-FW-RG, and select the fw-test-pol firewall policy.
- Select Application rules.
- Select Add a rule collection.
- For Name, type App-Coll01.
- For Priority, type 200.
- For Rule collection action, select Allow.
- Under Rules, for Name, type Allow-Google.
- For Source type, select IP address.
- For Source, type 10.0.2.0/24.
- For Protocol:port, type http, https.
- For Destination Type, select FQDN.
- For Destination, type
www.google.com - Select Add.
Azure Firewall includes a built-in rule collection for infrastructure FQDNs that are allowed by default. These FQDNs are specific for the platform and can't be used for other purposes. For more information, see Infrastructure FQDNs.
This is the network rule that allows outbound access to two IP addresses at port 53 (DNS).
- Select Network rules.
- Select Add a rule collection.
- For Name, type Net-Coll01.
- For Priority, type 200.
- For Rule collection action, select Allow.
- For Rule collection group, select DefaultNetworkRuleCollectionGroup.
- Under Rules, for Name, type Allow-DNS.
- For Source type, select IP Address.
- For Source, type 10.0.2.0/24.
- For Protocol, select UDP.
- For Destination Ports, type 53.
- For Destination type select IP address.
- For Destination, type 209.244.0.3,209.244.0.4.
These are public DNS servers operated by CenturyLink. - Select Add.
Reference:
1. https://www.petri.com/the-three-different-types-of-rules-that-are-in-the-azure-firewall
2. https://docs.microsoft.com/en-us/azure/firewall/features
3.https://docs.microsoft.com/en-us/azure/architecture/example-scenario/gateway/firewall-application-gateway
4. https://www.youtube.com/watch?v=uuojtUx-LOU&t=2s















Comments
Post a Comment